New Phishing Scam Uses Fake CAPTCHA Tests to Install Malware
Google Releases Open-Source Tool to Speed Up Android Security Patching
The Global Trail of Stolen Smartphones
Year-Long Attack Steals Credentials from Security Researchers and Hackers
Australia Leads the Way in Quantum-Resistant Cryptography
New Phishing Scam Uses Fake CAPTCHA Tests to Install Malware
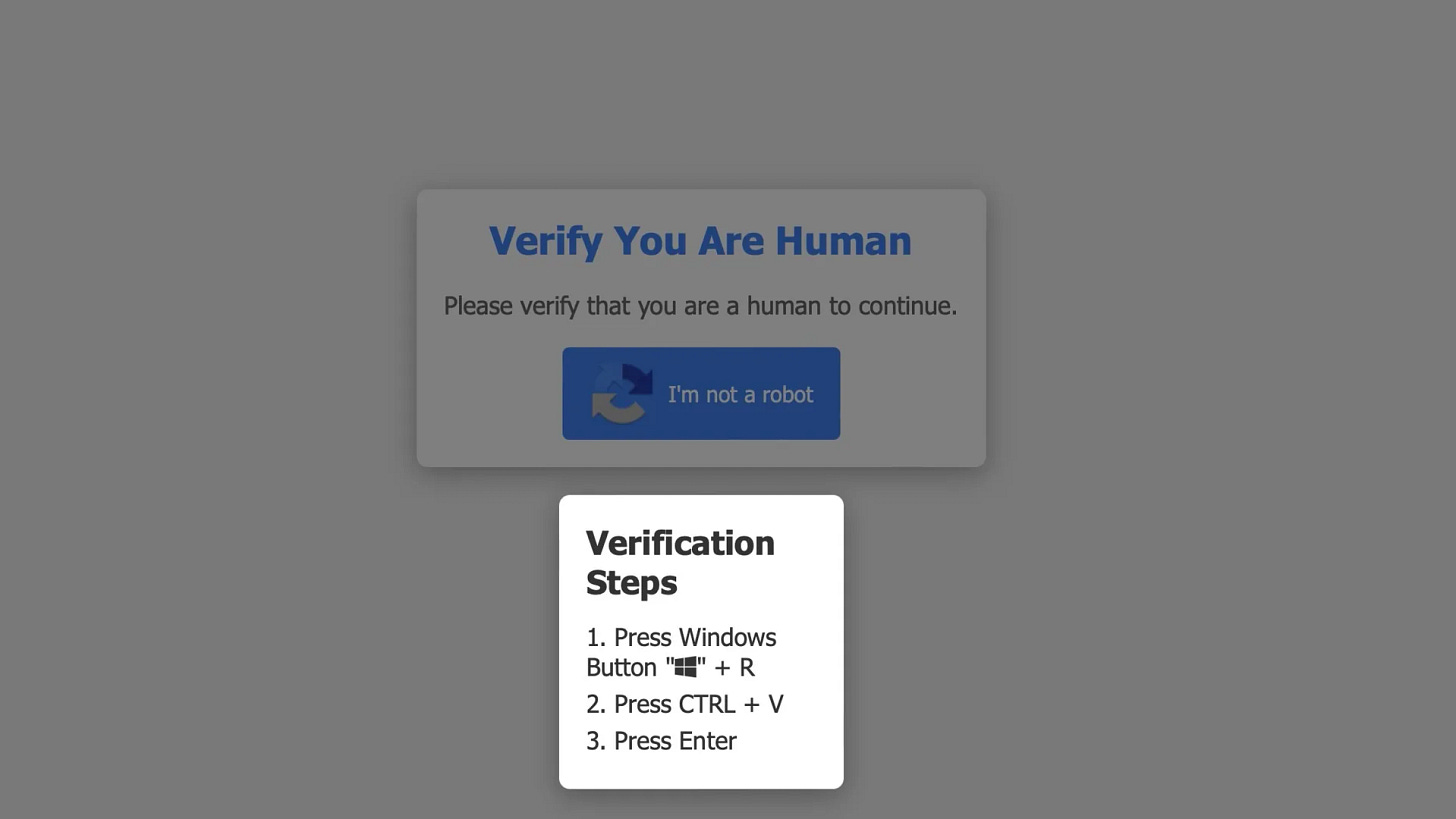
A new phishing scam is targeting unsuspecting users with fake CAPTCHA tests. These malicious tests, disguised as legitimate security measures, are designed to trick victims into installing malware on their devices.
How the Scam Works:
Fake CAPTCHA: Users encounter a fake CAPTCHA test on a malicious website.
Malicious Instructions: The CAPTCHA asks users to perform specific keystrokes, such as "Windows + R" followed by "Ctrl + V."
Malware Installation: These keystrokes execute a PowerShell script that downloads and installs the Lumma Stealer malware.
Data Theft: Once installed, the Lumma Stealer can steal sensitive information, including passwords, cookies, and cryptocurrency wallet details.
The Growing Threat of Phishing Attacks:
This latest phishing scam highlights the ongoing threat posed by cybercriminals who continuously evolve their tactics to target unsuspecting users. It's crucial to remain vigilant and exercise caution when encountering online requests, especially those involving unusual actions.
Tips to Protect Yourself:
Be Wary of Unusual CAPTCHAs, If a CAPTCHA test asks you to perform actions beyond simple image recognition, be suspicious. And avoid clicking on links in unsolicited emails or messages, even if they appear to come from a trusted source.
Google Releases Open-Source Tool to Speed Up Android Security Patching
https://security.googleblog.com/2024/12/announcing-launch-of-vanir-open-source.html
Google has released Vanir, a new open-source tool designed to streamline the process of identifying and applying security patches to Android devices.
The Problem:
The Android ecosystem relies on a complex update process where manufacturers must incorporate security fixes from Google and deploy them to individual devices. This process is time-consuming and labor-intensive, often leaving devices vulnerable for longer periods.
Vanir's Solution:
Vanir uses static code analysis to directly compare a device's code against known vulnerable code patterns. This approach avoids relying on unreliable metadata like version numbers and focuses on the actual code itself.
Benefits of Vanir:
Faster Patch Identification: Vanir automates the identification of missing security patches, significantly reducing the time it takes for manufacturers.
Improved Accuracy: Vanir boasts a 97% accuracy rate, minimizing false alarms and wasted effort.
Scalability: Vanir can be applied across diverse Android ecosystems and can be easily adapted to other platforms with minor modifications.
Open Source: By making Vanir open source, Google encourages collaboration and wider adoption within the security community.
Impact:
Vanir is expected to significantly improve the security posture of Android devices by enabling faster and more efficient deployment of critical security patches. This will ultimately benefit all Android users by reducing their exposure to vulnerabilities.
Availability:
Vanir is available now on GitHub under the BSD-3 license. The tool can be used as a standalone application or integrated into existing build systems.
The Global Trail of Stolen Smartphones
https://www.dailymail.co.uk/news/article-14165053/How-stolen-phone-ends-Chinas-Silicon-Valley.html
A Dark Journey from London Streets to Chinese Markets
The theft of mobile phones in major cities like London has become a significant global issue, with stolen devices often ending up thousands of miles away in China.
The Theft and Smuggling Process:
Street Theft: Phone snatchers, often operating in gangs, target unsuspecting victims in busy areas.
Handoff to Brokers: Stolen phones are quickly passed on to brokers, who may be involved in other criminal activities.
Securing the Device: To prevent tracking, the phones are placed in Faraday cages to block signals.
Shipping to China: The phones are shipped to China, often through intricate smuggling routes.
Repairs and Resale: In China, stolen phones are either sold as second-hand devices or disassembled for parts. Valuable components like gold, silver, and lithium-ion batteries are extracted.
The Impact on Victims:
Beyond the financial loss, victims of phone theft may also face privacy and security risks. Stolen phones can be used to access personal information, financial accounts, and social media profiles.
Combating the Problem:
Law enforcement agencies, technology companies, and governments are working together to combat phone theft and the global black market. Some strategies include:
Improved Tracking Technologies: Phone manufacturers are implementing advanced tracking and security features to deter theft and facilitate recovery.
International Cooperation: Law enforcement agencies are collaborating across borders to disrupt criminal networks involved in phone theft and smuggling.
Public Awareness Campaigns: Educating the public about the risks of phone theft and how to protect themselves.
While significant progress has been made, the global trade in stolen phones remains a complex issue. By understanding the methods used by criminals and the international supply chain, we can work towards more effective prevention and recovery strategies.
Year-Long Attack Steals Credentials from Security Researchers and Hackers
https://securitylabs.datadoghq.com/articles/mut-1244-targeting-offensive-actors/
Over 390,000 WordPress credentials and sensitive data stolen in a large-scale campaign targeting cybersecurity professionals.
A sophisticated cyberespionage campaign spanning over a year has compromised hundreds of systems belonging to security researchers, penetration testers, and potentially even malicious actors. Datadog Security Labs discovered the campaign, which is believed to be carried out by a threat actor tracked as MUT-1244.
Fake Exploits and Phishing Lured Victims
The attackers used a two-pronged approach:
Trojanized Repositories: They created fake repositories on GitHub containing malicious code disguised as proof-of-concept exploits for known vulnerabilities. Security professionals searching for exploit code unknowingly downloaded and executed the malware.
Phishing Emails: Phishing emails tricked victims into installing fake kernel updates that were actually malware.
Stolen Data Included SSH Keys and AWS Credentials
The malware targeted valuable data, including:
WordPress credentials (over 390,000 stolen)
SSH private keys
AWS access keys
Command history
Attackers Exploited Trust Within Security Community
The use of fake repositories on trusted platforms like GitHub allowed the attackers to exploit trust within the cybersecurity community. Additionally, some of the stolen credentials likely belonged to attackers who were using a tool called "yawpp" to validate stolen credentials. This suggests the attackers were targeting both legitimate security professionals and malicious actors.
Hundreds Still at Risk as Campaign Continues
Researchers believe hundreds of systems remain compromised, and the campaign is still ongoing. Security professionals and researchers are advised to be cautious when downloading code from untrusted sources and to be wary of unsolicited emails, even those seemingly related to security updates.
Australia Leads the Way in Quantum-Resistant Cryptography
Australia's Cyber Security Agency Accelerates Transition to Post-Quantum Cryptography
The Australian Signals Directorate (ASD) has announced plans to phase out traditional cryptographic algorithms like SHA-256, RSA, ECDSA, and ECDH in high-assurance cryptographic equipment by 2030. This move aims to proactively address the potential threat posed by quantum computing advances, which could render current encryption methods obsolete.
The Quantum Threat:
Quantum computers, once fully realized, have the potential to break current cryptographic standards, compromising sensitive data and systems. To mitigate this risk, the US National Institute of Standards and Technology (NIST) has developed new quantum-resistant algorithms.
Australia's Proactive Approach:
While NIST has set a 2035 deadline for transitioning to quantum-resistant cryptography, Australia is taking a more aggressive stance, aiming to complete the transition five years earlier for high-assurance systems. This proactive approach demonstrates Australia's commitment to cybersecurity and its recognition of the potential impact of quantum computing.
Challenges of the Transition:
The transition to post-quantum cryptography presents significant challenges, including:
Technical Complexity: Implementing new cryptographic algorithms requires careful planning and technical expertise.
Interoperability: Ensuring compatibility with existing systems and standards is crucial.
Security Risks: A poorly executed transition could introduce new vulnerabilities.
The Road Ahead:
As quantum computing technology continues to advance, it is essential for organizations to stay informed about the latest developments and to plan for a smooth transition to quantum-resistant cryptography. By taking proactive steps to adopt new standards, organizations can protect their sensitive data and systems from future threats.






Share this post