Disney Engineer's Life Destroyed by Malicious AI Download
Global Security Flaw Exposes Sensitive Employee Data and Physical Vulnerabilities
Malicious PyPi Package Pirating Deezer Music for Years
Code Security Remains Crucial, Even in Hardened Environments
Google Introduces AI Scam Detection for Android2025_03_07 - Google
Disney Engineer's Life Destroyed by Malicious AI Download
https://www.wsj.com/tech/cybersecurity/disney-employee-ai-tool-hacker-cyberattack-3700c931
A former Disney engineer, Matthew Van Andel, had his life turned upside down after downloading a seemingly harmless AI tool from GitHub. The software, intended for creating AI images, contained malware that granted hackers access to his computer and sensitive data.
The hackers stole his Disney login credentials, leading to the leak of over 44 million Disney internal slack messages, including customer information, employee passport numbers, and financial data. They also accessed his personal accounts, stealing credit card numbers, leaking his social security number, and even gaining access to his home Ring cameras.
Matthew was subsequently fired from Disney after a forensic analysis of his work computer found he had accessed pornographic material, which he denies. He lost his health insurance and $200,000 in bonuses.
The incident highlights the dangers of downloading software from untrusted sources and the vulnerability of personal and corporate data to sophisticated cyberattacks. Lot of people think that content from GitHub are trustworthy and they couldn't be more wrong. Matthew's case underscores the importance of strong password security, two-factor authentication, and vigilance against malicious software. He was using 1Password as his password manager but didn't have any 2FA access on it.
Global Security Flaw Exposes Sensitive Employee Data and Physical Vulnerabilities
https://www.modat.io/post/doors-wide-open-critical-risks-in-ams
A widespread security risk has been discovered involving misconfigured and exposed Access Management Systems (AMS) across numerous industries and countries.
This exposure has resulted in hundreds of thousands of employee records, including personal identification details, biometric data, photographs, and work schedules, being accessible online. Additionally, the physical security of thousands of organizations has been compromised, allowing potential unauthorized entry into buildings and bypassing physical security measures.
The affected sectors include construction, healthcare, education, manufacturing, oil, and government entities, with a high concentration of exposed systems found in European countries, the US, and the MENA region.
The consequences of these vulnerabilities range from financial losses and regulatory penalties, such as GDPR fines, to severe breaches leading to identity theft, unauthorized access, and disclosure of confidential business information.
The report emphasizes the critical need for organizations to implement robust security measures, including restricting internet access to AMS, regularly updating security patches, changing default credentials, and implementing continuous monitoring to protect sensitive data and maintain physical security.
Malicious PyPi Package Pirating Deezer Music for Years
https://socket.dev/blog/malicious-pypi-package-exploits-deezer-api-for-coordinated-music-piracy
A PyPi package named 'automslc,' downloaded over 100,000 times since 2019, has been pirating music from the Deezer streaming service using hardcoded credentials.
The package bypasses Deezer's limitations and downloads full-length, high-quality audio files for offline listening and distribution, violating Deezer's terms of service and copyright laws.
Security firm Socket discovered the package, noting that while it functions as a piracy tool, it also utilizes command-and-control infrastructure, potentially turning users into a distributed network.
This raises concerns about the potential for the tool to be repurposed for other malicious activities.
The package remains available on PyPi at the time of reporting, and users are warned of the legal risks associated with its use.
Code Security Remains Crucial, Even in Hardened Environments
https://www.sonarsource.com/blog/why-code-security-matters-even-in-hardened-environments/
A recent study demonstrates that even in hardened environments with read-only file systems, attackers can exploit file write vulnerabilities in Node.js applications to achieve remote code execution. This is accomplished by manipulating exposed pipe file descriptors, bypassing typical security restrictions.
The research highlights the limitations of infrastructure hardening as a sole security measure. Attackers can leverage vulnerabilities in the application's source code, even when the underlying infrastructure is fortified.
The attack involves writing crafted data structures to anonymous pipes used by Node.js's event loop, ultimately triggering the execution of arbitrary code. This technique exploits the "everything is a file" philosophy in Unix-based systems and demonstrates the importance of code security.
Key findings include:
Bypassing Read-Only Restrictions: Attackers can write to pipe file descriptors, even when the file system is mounted read-only.
Manipulating Event Handlers: Attackers can craft data structures to manipulate Node.js's event handler and execute arbitrary code.
The Importance of Code Security: Infrastructure hardening alone is insufficient; vulnerabilities in the source code must be addressed.
This research underscores the need for developers to prioritize code security, even in environments with robust infrastructure hardening. Vulnerabilities at the source code level can be exploited, regardless of other security measures.
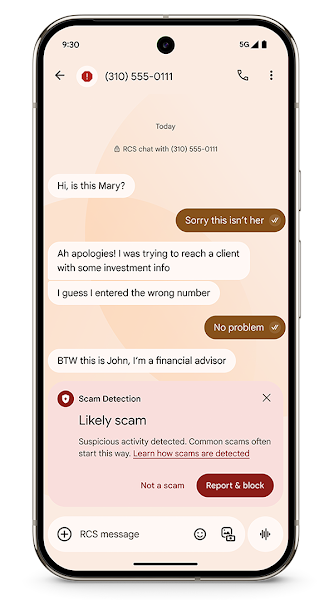
Google Introduces AI Scam Detection for Android
https://security.googleblog.com/2025/03/new-ai-powered-scam-detection-features.html
Google has launched AI-powered scam detection features for Android devices, designed to protect users from conversational fraud. These features target scams that start innocently but escalate into harmful situations, as well as phone call scams using spoofed numbers.
Google partnered with financial institutions to develop AI models that can identify suspicious patterns in conversations and provide real-time warnings. These models operate entirely on-device, ensuring user privacy. Users can choose to dismiss or report and block suspicious senders. The feature is enabled by default for conversations with unknown numbers.
A similar AI-powered scam detection feature for phone calls is being expanded to English-speaking Pixel 9+ users in the U.S. This feature, which is optional, processes call audio ephemerally and notifies participants when it is active.
These developments follow Google's announcement that over one billion Chrome users are using Enhanced Protection mode, which utilizes AI and machine learning to detect phishing, social engineering, and scam techniques.











Share this post